Why Data Security in Healthcare Is More Critical Than Ever
Healthcare isn’t just digitizing, it’s under siege. One breach can mean millions in losses, irreparable damage to patient trust, and regulatory fallout that echoes far beyond IT. As digital transformation accelerates, the stakes for healthcare data security have never been higher.
Healthcare organizations manage some of the most sensitive data imaginable—and they are increasingly in the crosshairs of cybercriminals. The question isn’t whether your systems will be targeted. It’s whether you’ll be ready.
What Is Healthcare Data Security?
Healthcare data security refers to the strategies, technologies, and protocols used to protect sensitive health information—including electronic health records (EHRs), billing data, patient identities, and more—from unauthorized access, breaches, and loss.
This practice combines physical safeguards, digital protections, and human protocols to secure data across its lifecycle: from collection and storage to transmission and deletion.
Why Data Security Is Critical in Healthcare
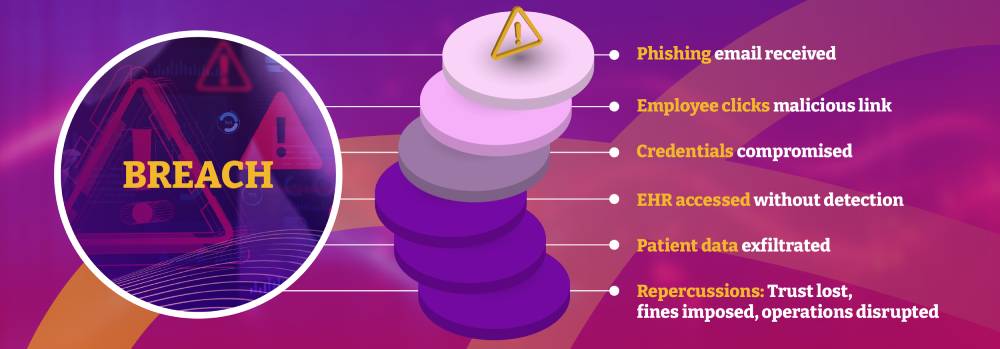
A single breach can expose thousands of patient records, opening the door to identity theft, insurance fraud, and medical misinformation. But the consequences don’t stop there:
- Loss of patient trust: Patients may hesitate to share critical health information if they fear it won’t be protected.
- Financial repercussions: Healthcare data breaches cost an average of $10.93 million per incident, the highest of any industry.
- Regulatory penalties: HIPAA, HITECH, and other frameworks impose steep fines for non-compliance.
Data security in healthcare is more than a compliance checkbox—it’s a foundation for clinical and operational integrity.
Common Threats to Healthcare Data Security
Healthcare systems face a unique mix of internal and external threats:
- Phishing Attacks: Fraudulent emails that trick employees into revealing login credentials or downloading malware.
- Ransomware: Malicious software that locks down systems until a ransom is paid, often paralyzing operations.
- Insider Threats: Employees or contractors who mishandle or misuse access to sensitive data, whether accidentally or maliciously.
- Third-party Vulnerabilities: Vendors with inadequate security controls that create weak links in the data chain.
- Lost or Stolen Devices: Unsecured mobile devices, laptops, or USB drives that contain sensitive information.
- Outdated Software: Legacy systems with known vulnerabilities that lack modern security patches.
Each of these threats requires a proactive, multilayered defense strategy to prevent breaches before they start.
Common Healthcare Data Security Challenges
Despite the high stakes, many organizations struggle to keep pace:
- Outdated Infrastructure: Legacy systems may lack encryption, multifactor authentication, or update capabilities.
- Limited Resources: Smaller practices often lack full-time security staff or budgets to invest in best-in-class tools.
- Staff Awareness: Even the best tech can’t stop a breach caused by human error. Staff often lack training on safe data practices.
- Complex Regulations: Navigating overlapping federal, state, and local privacy laws is difficult—and mistakes can be costly.
These challenges highlight the need for scalable, automated, and compliance-ready solutions.
Best Practices for Strengthening Healthcare Data Security
Building a robust healthcare data security strategy requires a layered approach:
- Data Encryption: Encrypt sensitive data both at rest and in transit to protect it from interception.
- Access Controls: Limit data access based on user roles and require strong authentication.
- Employee Training: Educate staff regularly on phishing prevention, password hygiene, and breach reporting protocols.
- Regular Audits: Conduct risk assessments, penetration testing, and vulnerability scans.
- Secure Cloud Storage: Partner with HIPAA-compliant cloud providers with robust access management and monitoring tools.
- Incident Response Plans: Have a documented, tested plan in place to act quickly if a breach occurs.
- Vendor Management: Vet third-party vendors thoroughly and monitor their access to systems and data.
Security isn’t just about protection—it’s about resilience and trust.
The Role of Technology in Healthcare Data Security
Advanced technologies now play a critical role in protecting patient information:
- EHR Systems: When properly configured, EHRs include audit trails, role-based access, and automated alerts.
- Artificial Intelligence: AI can detect anomalies, flag suspicious activity, and accelerate threat response.
- Cloud Platforms: Secure, scalable, and redundant cloud environments reduce risk and support disaster recovery.
But tech alone isn’t enough. Success depends on how these tools are implemented, monitored, and governed.
How Madaket Health Can Help Secure Your Healthcare Data
Madaket Health offers secure, automated solutions built for healthcare workflows. From provider directory management to payer enrollment, we ensure sensitive data is handled with precision and compliance.
Our platform:
- Operates within secure, HIPAA-compliant environments
- Minimizes manual data handoffs that increase breach risk
- Automates credentialing and enrollment workflows to reduce exposure
- Delivers a centralized platform for better data governance and visibility
Healthcare organizations using Madaket reduce security risks while reclaiming operational bandwidth. Explore our Platform to see how we can support your security and compliance goals.
Conclusion
As the digital front door of healthcare expands, so does the attack surface. Organizations that treat healthcare data security as a strategic imperative—not just an IT function—will be better equipped to serve patients, earn trust, and thrive.
It’s not a matter of if you’ll be targeted, but when. Now is the time to invest in smart, scalable, and resilient security infrastructure.
FAQ
It refers to protecting sensitive patient information from unauthorized access, breaches, or misuse using a combination of technical and administrative safeguards.
Human error, particularly phishing attacks and misconfigured systems, remains the most common and damaging threat.
Because compromised data can lead to patient harm, financial penalties, reputational damage, and loss of public trust.
© 2024 Madaket Health | Privacy Policy | Terms & Conditions
